| –ù–∞–∑–≤–∞–Ω–∏–µ | : | IPsec, Tunnelling and VPNs (ITS335, L27, Y14) |
| –ü—Ä–æ–¥–æ–ª–∂–∏—Ç–µ–ª—å–Ω–æ—Å—Ç—å | : | 22.54 |
| –î–∞—Ç–∞ –ø—É–±–ª–∏–∫–∞—Ü–∏–∏ | : | |
| –ü—Ä–æ—Å–º–æ—Ç—Ä–æ–≤ | : | 1¬Ýrb |




|
|
Steventhis is just an awesome way to explain Comment from : Pradeep Agarwal |
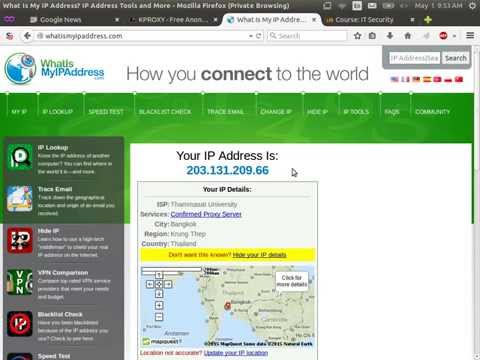 |
Internet Privacy Options (ITS335, L27, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
 |
Web Proxies, VPNs and Tor (ITS335, L28, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
 |
Tunnels, VPNs and IPsec (ITS335, L23, Y15) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
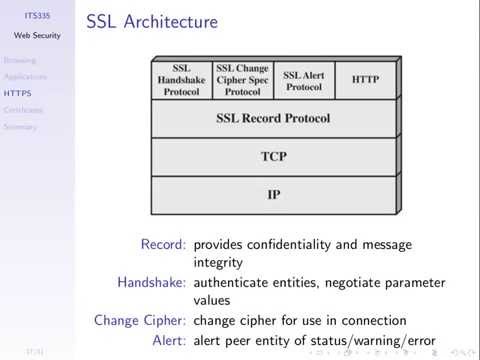 |
Web Browsing and HTTPS (ITS335, L20, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
 |
Web Security Attacks (ITS335, L24, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
 |
Introduction to IT Security (ITS335, L1, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
 |
Summary on Top 10 Web Attacks (ITS335, L26, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
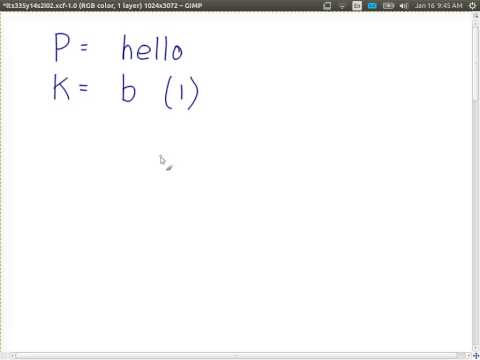 |
Encryption Techniques (ITS335, L2, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
 |
Password Storage Approaches (ITS335, L8, Y14) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |
 |
Tunnelling with SSH (CSS441, L25, Y15) –Ý—ï–°‚Äö : Steven Gordon Download Full Episodes | The Most Watched videos of all time |